Just in time for Halloween, the Washington Post has brought us a horror story about U.S. and U.K. intelligence agencies reading massive amounts of private data directly off of the internal communications infrastructure of U.S. Internet giants Google and Yahoo.
The Post's report reveals that the spy agencies tapped into the internal, private fiber-optic links between the companies' data centers. This gave the spooks a view into corporate and customer data moving between data centers—data that the companies likely didn't encrypt because they viewed these dedicated private links as secure. That means that the private communications of millions of ordinary users, both foreign and domestic, were exposed to surveillance by the intelligence agencies.
A chilling back-of-the-napkin sketch obtained by the Post depicts user data protected by SSL/TLS encryption as it traveled over the public Internet—but unprotected and exposed to spying within the companies' internal infrastructure.
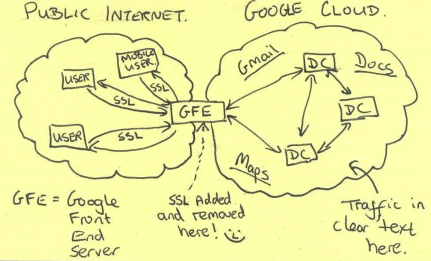
What does this mean for ordinary users?
The story suggests that the user data (including the text of chats and e-mails, as well as metadata about users' relationships and whereabouts) probably was intercepted as it flowed over the private links. There's no way to know exactly whose data was intercepted, but potentially all users of these services—or other services that may have been attacked in the same way—could have had their data monitored.
Google, at least, said last month that it was deploying more encryption internally to protect against this monitoring in the future. In a statement issued today, Google's chief legal officer, David Drummond said, “We have long been concerned about the possibility of this kind of snooping, which is why we continue to extend encryption across more and more Google services and links.” A Yahoo spokesperson said, “We have strict controls in place to protect the security of our data centers, and we have not given access to our data centers to the NSA or to any other government agency.” Yahoo has not yet clarified whether it will take new technical measures to protect against this spying.
Users who used third-party encryption software like OTR to encrypt their messages may have been partially protected because their intercepted communications would still have been encrypted as they transited the companies' internal networks.
The materials published by the Post suggest that the SSL/TLS encryption used to protect users' data on sites that use HTTPS provides privacy and security benefits: the author of the spooky napkin sketch implicitly regards it as non-trivial for NSA to remove this encryption. That's why NSA would rather go around it and try to access our communications after they've already been decrypted.
What should technology companies do about this kind of monitoring?
This reporting goes to show that the intelligence agencies are sophisticated attackers that are prepared to find and take advantage of the weakest link in a chain of protections. So companies need to examine the entire set of protections that apply across their infrastructure, to identify and address the weak links. One specific precaution that would be valuable for companies with their own distributed data centers is to ensure that they're using state-of-the-art VPNs or link encryption between their facilities. Indeed, encryption even between the devices within a data center may be an important precaution if the routers and switches connecting those devices can be targeted with malware—though such attacks don't appear to be part of the monitoring revealed by the Post.
These attacks remind us that there are many ways that a network can be untrustworthy, and that encryption is the main technology we have for keeping data safe on untrustworthy networks. Now is a great time to think about how we can use more encryption and make sure that we're using it correctly.










