The warrant the FBI used in the Playpen investigation—which resulted in the delivery of malware to over a thousand computers, located around the world—violated Rule 41, an important rule of federal criminal procedure. Although Rule 41 may seem obscure, it plays a vital role in limiting when federal law enforcement agencies can conduct lawful searches and seizures.
More in this series:
The Story of the FBI’s Unprecedented and Illegal Hacking Operation
Some Fourth Amendment Basics and Law Enforcement Hacking
Why the Warrant to Hack in the Playpen Case Was an Unconstitutional General Warrant
The warrant used in the Playpen investigation is an omen of warrants to come. That’s because DOJ is advocating for a change to Rule 41 that, if it takes effect, was designed to authorize exactly this kind of warrant.
Let's take a look at Rule 41, what happened in the Playpen case, and the changes DOJ is trying to make to the rule—changes that must be stopped.
What is Rule 41?
Rule 41 is a part of the Federal Rules of Criminal Procedure—a set of rules that govern criminal investigations and prosecutions in the federal court system. Rule 41 authorizes federal magistrate judges (a specific type of federal judge) to issue search warrants for federal law enforcement.
One important restriction in the rule deals with where the warrant application must be made. Right now (and subject to a few exceptions that aren’t relevant here), Rule 41 only authorizes magistrate judges to issue warrants to conduct searches in the judicial district where the magistrate is located. So, for example, if the FBI wants to search a house in San Francisco, it must apply for a search warrant in the Northern District of California—not the Western District of Texas.
This “territorial” restriction is an important one. It ensures that any search or seizure that is authorized has a sufficient nexus to the judicial district, and it helps guard against law enforcement “forum shopping”—where law enforcement is able to seek out sympathetic or unquestioning judges to obtain warrants, even if those warrants have little or no connection to the judicial district.
Why did the Playpen warrant violate Rule 41?
In the Playpen case, the FBI blew straight through that territorial limitation. The FBI went to a magistrate judge in the Eastern District of Virginia and asked her to sign off on a warrant that would allow them to deliver malware to search any computer that accessed Playpen—no matter where the computer was located.
And the FBI did just that, searching computers located in Arkansas, California, Louisiana, Massachusetts, Oklahoma, Ohio, Pennsylvania, Texas, Washington, and Wisconsin—just to name a few examples.
Under the terms of Rule 41, the magistrate could only authorize searches that occurred in the Eastern District of Virginia (save those irrelevant exceptions). But remember: because users were accessing the site through Tor, the FBI didn’t know where its searches would take place. That means a user might have accessed the site, and searches might have been carried out next door, the next city over, the next state over, or the next country over. There’s evidence, in fact, that the FBI did conduct international searches. These types of international searches are particularly problematic because many countries have laws prohibiting precisely this type of hacking.
If the FBI didn’t know where its searches would occur, then why did the magistrate issue the warrant? The short answer: the FBI misled the judge. As you can see below, the warrant application clearly states that the searches will be carried out on "persons or property . . . located in the Eastern District of Virginia[.]"
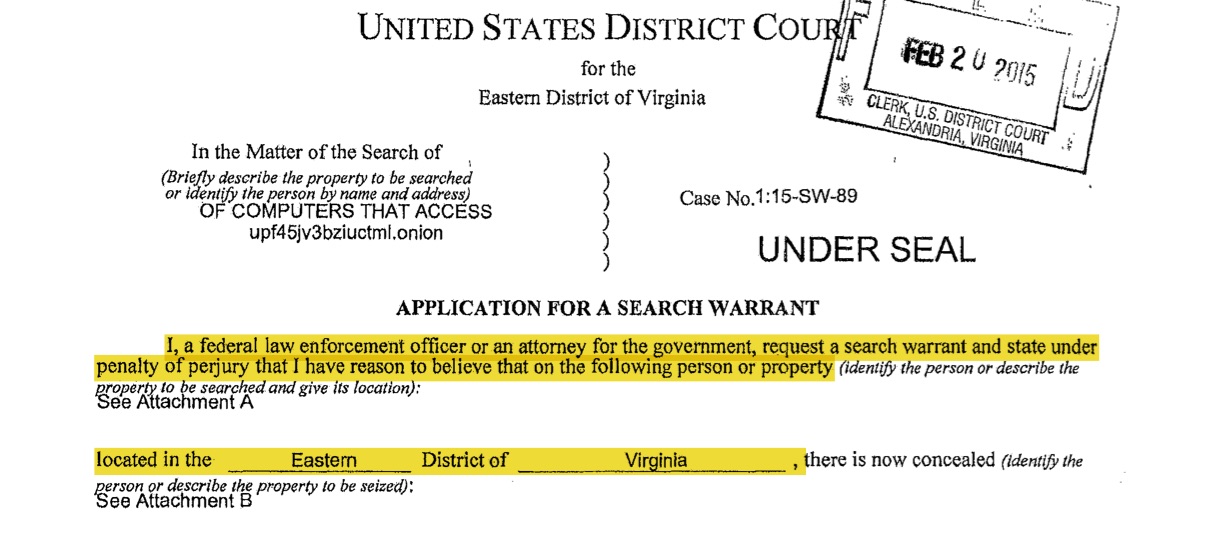
That was not true, and the FBI knew it. Had the FBI filled out the warrant application honestly, making clear that it did not know where its searches would be carried out, there's a good chance the magistrate would not have issued the warrant in the first place. In fact, one court reviewing the issue said exactly that, finding that "had [the Magistrate judge] understood that the NIT technology would search computers in other districts. . . she probably would not have issued the NIT Warrant given the limitations of the Rule."
The FBI also did not bother to mention that the magistrate was authorizing activities that would likely violate the laws of other countries—a convenient omission, to say the least. Yet this is all information the federal judiciary needs when it is signing off on warrants, especially ones authorizing a surveillance technique as novel as the one used here.1
Fortunately, almost every federal court that we know of that has looked at the issue has recognized that the warrant ran afoul of Rule 41, although the courts have disagreed about whether the violation requires suppression of the evidence obtained through the search. In our view, this kind of misrepresentation from federal law enforcement shouldn't be tolerated by the courts. The only option is suppression.
So how does the proposed change to Rule 41 figure into this, and how will this affect Internet users more generally?
As we’ve written about before, DOJ is pushing a change to Rule 41. The new Rule 41 would, for the first time, authorize magistrates to issue search warrants, like the Playpen warrant, when “technological means” like Tor or VPNs are obscuring the location of a computer, or when a computer is swept up in a "botnet." In these circumstances, law enforcement could remotely access, search, seize, or copy data on computers, no matter where the computers were located and without providing notice to the users being searched. That means the FBI could go to almost any federal magistrate judge and get a warrant authorizing the FBI to hack into a computer (or, as was the case in the Playpen investigation, thousands of computers), no matter where in the world those computers are located.
Make no mistake: the changes to Rule 41 will result in many, many more warrants like the one used in the Playpen case. "Fine," you might say, "I'm not doing anything illegal online. The FBI won't have any interest in hacking into my computer." But, because the Rule 41 changes authorize hacking when a computer is part of a botnet, even innocent users caught up in a botnet could be unknowingly subjected to an FBI search.
Perhaps that's all fine and good, if there were strict limitations on the circumstances the FBI could use this authority, the information they could obtain from searches, and mandatory transparency about when and where these techniques are used (among other concerns). But right now, there is very little cabining law enforcement's authority. The FBI is making up the rules as it goes along. And, and as we've blogged about before, courts looking at the Playpen cases are struggling mightily in applying traditional legal rules, like the Fourth Amendment, to the government's new hacking techniques.
With the courts struggling to place appropriate limitations (and the FBI suffering from serious deficits in candor), right now is not the time to massively expand the government's authority to hack into private computers. Congress cannot expand the government's authority without establishing rules to govern (and limit) that authority. That’s why we need your help in speaking out against the changes to Rule 41.
- 1. Admittedly, the FBI's affidavit in support of the warrant application provided the magistrate with more information about how the malware would operate. However, even that more detailed affidavit: (1) only mentioned one location, the Eastern District of Virginia, (2) never mentioned that the great majority of users of the site were possibly, if not probably, located outside the judge's jurisdiction, and (3) nowhere makes clear that the FBI does not know the actual location of the users. Instead, the affidavit and application appear designed to obscure, rather than acknowledge, the fact that the searches will occur outside EDVA.






